
Module 17 B Professional Education Questionaires Certificate of Professional Course in
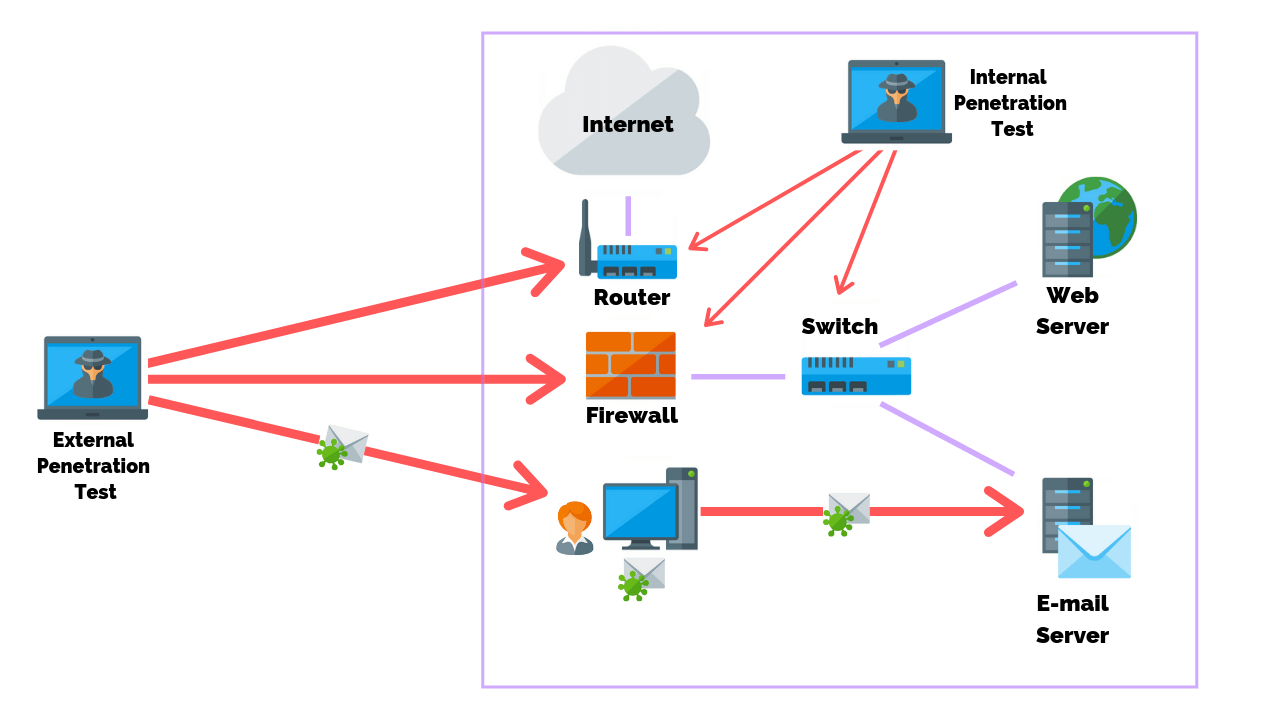
MegaCorpOne Penetration Test Report 2. Introduction In accordance with MegaCorpOne's policies, SafeHouse Security, LLC (henceforth known as Safe House Security conducts external and internal penetration tests of its networks and systems throughout the year. The purpose of this engagement was to assess the networks' and systems' security.
PPT Testing Report PowerPoint Presentation, free download ID5882461
MegaCorpOne Penetration Test Report 9 Executive Summary Narrative STX applied the five steps of a penetration testing engagement and found numerous weaknesses and vulnerabilities, summarized below. Specific technical information about each vulnerability, including screenshots, can be found starting on page 12.

CPENT (Certified Testing Professional) The Ultimate Pentesting Certification
This is the report I made for MegaCorpOne (simulated penetration test). This report contains screenshots of vulnerabilities and exploits that I was able to find using Kali inside an Azure virtual Machine. I used a combination of SQL Injections, Metasploit, and Nessus to get the results that I got. Check out my report to learn more!
Online Test Telegraph
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window.

(PDF) Exploiting Vulnerabilities of a Linux Based Machine Testing Report and
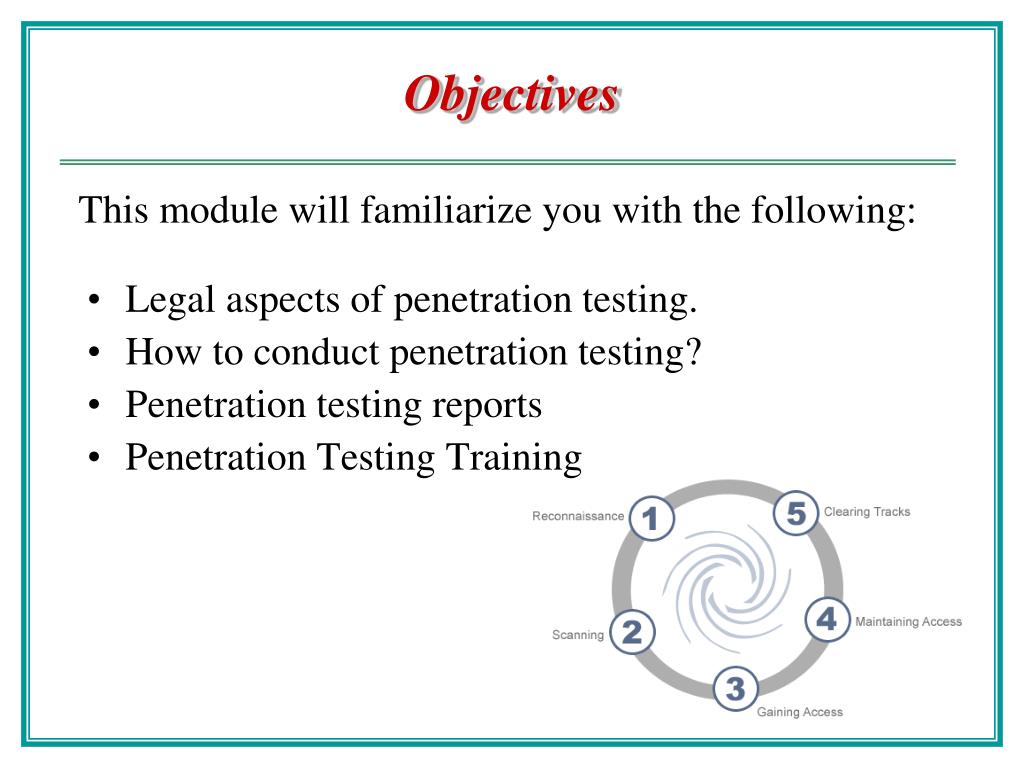
Introduction. Penetration testing is a vital method to evaluate the security of an organization. By attempting to exploit potential security weaknesses of all kinds, from misconfigurations to end user mistakes, organizations can proactively take action before an attack occurs. Having spent over two decades observing and participating in the.

Web Application Testing Complete Pen Testing Report
My first attempt at a penetration test, as well as a following report. - FRiggitsXx/MegaCorpone_Report.. My first attempt at a penetration test, as well as a following report. Black box test This project was simulated inside a microsoft azure-lab Kali-Linux VM inside a Hyper-V Manager. This composed of Penetration testing a brand named.
UNIT 17 Homework Test Engagement GoodSecurity Test Report Studocu
MegaCorpOne Penetration Test Report 6 Penetration Testing Methodology Reconnaissance CyberNinja Security begins assessments by checking for any passive (open source) data that may assist the assessors with their tasks. If internal, the assessment team will perform active recon using tools such as Nmap and Bloodhound.
Geosciences Free FullText CPT Data Interpretation Employing Different Machine Learning
MegaCorpOne Penetration Test Report 5 Introduction In accordance with MegaCorpOne's policies, Cybertek, LLC (henceforth known as CTK) conducts external and internal penetration tests of its networks and systems throughout the year. The purpose of this engagement was to assess the networks' and systems' security and identify potential security flaws by utilizing industry-accepted testing.

Btpsec Sample Test Report
Homework: Penetration Test Report. In this activity, you will record your activities and form a report that will be turned in as a deliverable to the CISO of MegaCorpOne. Remember that the report is the most important part of an engagement, as it is a story of what findings you discovered and how you discovered them.

PT Testing Report (sample)
We used our proven vulnerability testing methodology to assess all relevant web applications, networks, and systems in scope. Rekall has outlined the following objectives: Table 1: Defined Objectives. Objective Find and exfiltrate any sensitive information within the domain. Escalate privileges. Compromise several machines. Penetration Testing.

Security Test Report on CIS (Corporate Information Systems) 2017 attack scenarios
The Statement of Work (SOW) is a document that defines the expectations for a specific business arrangement and includes a list of deliverables, responsibilities of both parties, payment milestones, schedules, and other terms. Lesson 17: Communicating During the PenTesting Process Learn with flashcards, games, and more — for free.
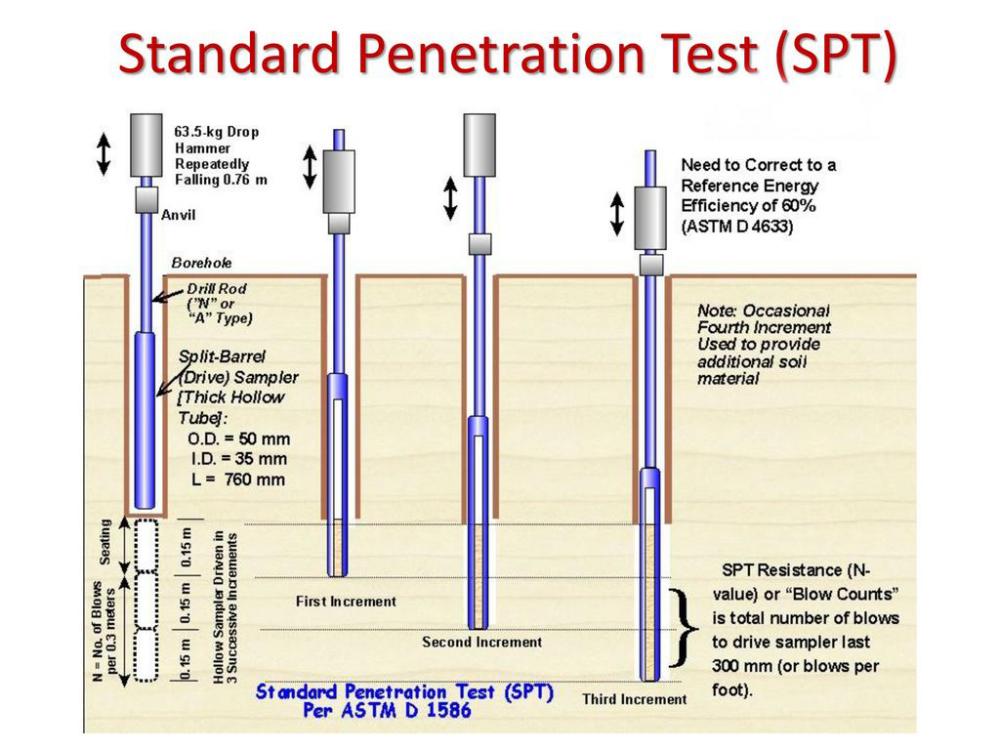
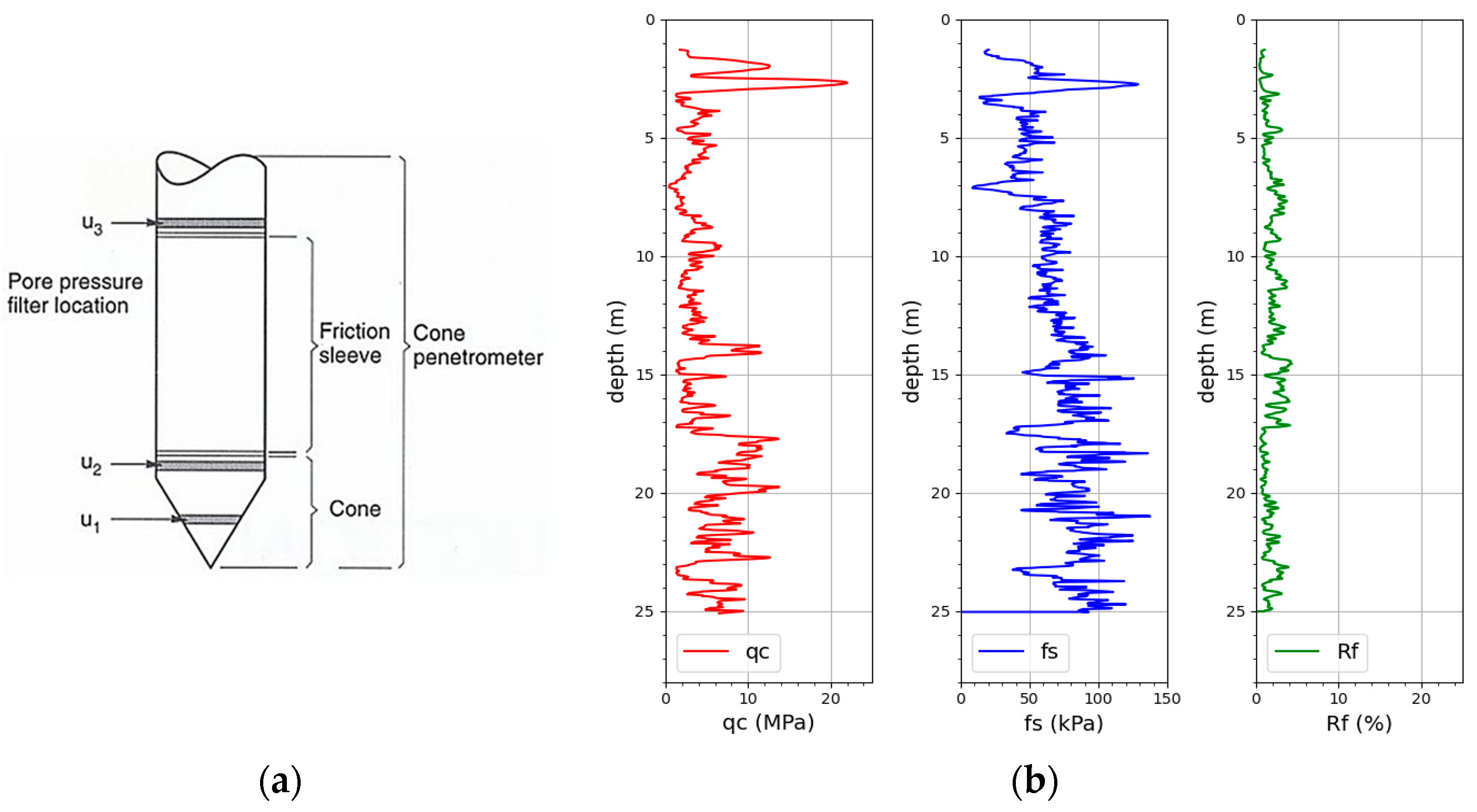
Kinds of Standard SPT Testing Kit for Soil Prospecting, Wholesale Standard
In this module, students will write a penetration testing report based on the challenges from the penetration test completed in Module Q (Penetration Testing: Bringing It All Together). A sample penetration testing report is provided to help guide students through the process. Educators will act as the client and provide students with direction and expectations.

Testing with Kali Linux 2023 released New modules, exercises, challenges (PEN200
conducts external and internal penetration tests of its networks and systems throughout the year. The purpose of this engagement was to assess the networks' and systems' security and identify potential security flaws by utilizing industry-accepted testing methodology and best practices.
PenTestHub Testing Report v.1.0 Pentest reports
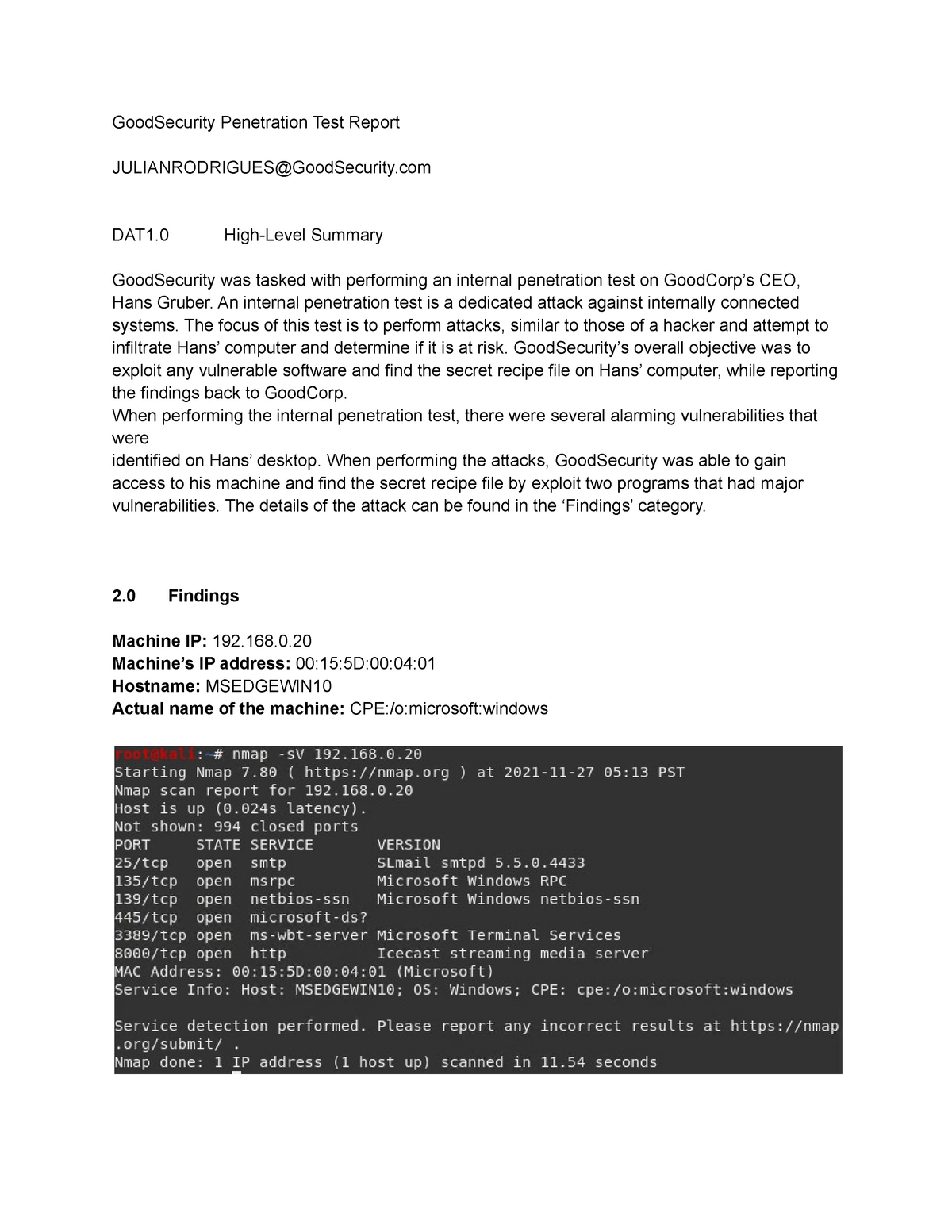
GoodSecurity Penetration T est Report. JULIANRODRIGUES@GoodSecurity .com. DA T1.0 High-Level Summary. GoodSecurity was tasked with performing an internal penetration test on GoodCorp' s CEO, exploit any vulnerable software and find the secret recipe file on Hans' computer, while reporting. When performing the internal penetration test.

How To Use The Metasploit Framework For Testing
Penetration Test Report MegaCorp One August 10th, 2013 Offensive Security Services, LLC 19706 One Norman Blvd. Suite B #253 Cornelius, NC 28031 United States of America Tel: 1-402-608-1337 Fax: 1-704-625-3787. this updated exploit will be provided separately from this report.

9 Testing Types
Search for the Icecast module and load it for use. Run the command to search for the Icecast module: Answer: Run the command to use the Icecast module: Note: Instead of copying the entire path to the module, you can use the number in front of it. Answer: Set the RHOST to the target machine. Run the command that sets the RHOST: Answer: Run the.
- Where To Watch Border Security
- Weather In Canley Heights 10 Days
- Narnia Voyage Of The Dawn Treader Actors
- Cast Of The Accountant 2
- Is Lyons An Irish Name
- Chris Colfer The Land Of Stories The Wishing Spell
- King S Birthday Honours List 2023
- Sea Lake Caravan Park Victoria
- What Does A Redback Spider Eat
- When Is Reputation Tv Coming Out